Appsec tools for enterprise
Finally, proactive application security programs made for enterprise
No more hours spent manually chasing vulnerabilities. Mend.io helps enterprise development and security teams detect code vulnerabilities in near real-time, remediate threats automatically with a single click, and get full visibility into the entire risk posture.
Trusted by enterprise teams
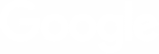



The solution
Why enterprise software and security teams choose Mend.io to proactively manage application risk
Proactive vulnerability detection
With a low false positive rate, Mend.io proactively scans code bases for vulnerabilities, analyzes them for update safety, and automatically issues pull requests helping developers eliminate manual work and act quickly to keep their code bases secure and compliant.
Integrates with your workflows
Mend.io scans support 27 programming languages and frameworks, work locally and in the cloud so it doesn’t leave your premises, and integrate with your existing DevOps environment.
Full visibility into risk posture
Security teams have access to in-depth reports and dashboards including the dependencies that need updated across all applications, license management for any new or existing code base component, and SBOMs that scan both direct and transitive dependencies.
Explore Mend.io’s enterprise AppSec platform
No matter your application, Mend.io has you covered
Proactive AppSec. One price.
$1,000
per developer • per year
Volume pricing available.
Frequently asked questions
Where does the vulnerability information come from?
The Mend.io database is the largest and most mature database of open source vulnerabilities. It contains more than 300,000 vulnerable components which are aggregated from the CVE/NVD, and various other sources like the GitHub issue tracker, security advisories, and open source projects issue trackers. Mend.io uses a proprietary patented algorithm that matches between vulnerability and only the impacted version, thus guaranteeing no false positives that waste developers’ time.
How does your SCA product work?
Our plugins integrate with your repositories, build tools, CI servers and more. It calculates the digital signature for all your components without ever scanning your code. It then cross-references the digital signatures with the ones in the Mend.io database to detect the open source components in your products. An immediate up-to-date report is generated with all components and issues detected.
If you have integrated Mend SCA with your build pipeline, the report is generated every time you run your build. If you have integrated Mend SCA with your developers’ repo, Mend SCA detects and displays vulnerabilities immediately when the code is written and/or committed to the repo.
How does your SAST product work?
Our SAST product uses a hybrid architecture. It scans your software locally, so your source code never leaves your premises. Analysis, auto-remediation, reporting and other functions are done in the cloud. This gives you the best of both worlds — peace of mind of an on-premises scanner, with no administrative or maintenance headaches.
Can you enforce customized policies and how do you enforce it?
Yes, Mend.io enforces policies automatically throughout the software development process. You can define your policies according to security vulnerabilities severity, open source license type, software bugs severity, age of a component and many more. You can approve, reject, initiate an approval flow or open an issue ticket based on your criteria and definitions.
In addition, Mend.io also offers a browser extension, which notifies your developers if a certain component meets your organization’s policies before downloading the component.
What type of reports do you offer?
We offer a variety of reports that will help you monitor all of your open source activity such as an inventory report, due diligence report, high severity bugs report, vulnerability report and many more.
Can I still use your AppSec platform if my environment is not connected to the internet?
Some plug-ins for Mend SCA can be used in isolated environments by generating an update request and saving the request locally as a text file. For these plug-ins, the file can later be moved to an online environment for automatic or manual updates.
Does Mend.io identify risks in both direct and transitive dependencies?
Yes, Mend.io conducts deep scans of open source code to identify risks in direct and transitive dependencies, and produces a compliance report related to standards by NIST
Thanks for requesting a demo.
An account manager will be in contact shortly.
Get started
See how Mend.io can help you proactively manage application risk
Mend offers an enterprise suite of application security tools to help you detect and remediate vulnerabilities in your open source while maintaining full visibility into your entire security risk posture.
Here’s what you can expect after filling out the form:
- An expert on our team will reach out to you
- We will schedule a quick discovery call on your use cases
- We will then schedule a customized demo for you







