Open source risk management for AI driven development
Mend SCA protects AI native applications by identifying and mitigating open source risks, strengthening your AI initiatives and ensuring your models and data stay protected from emerging threats.
Trusted by enterprise teams



The solution
Why enterprise teams choose Mend SCA to proactively manage risks across their open source dependencies
Agentic SCA delivery for AI code assistants, before code submission
Autonomously find and fix open source vulnerabilities, before committing to the repo.
Mend SCA feeds vulnerability information with reachability analysis into AI code assistants for rapid remediation of open source vulnerabilities, directly in the AI workflow.
Identify & prioritize dependency risk
Mend SCA scans for vulnerabilities in your direct and transitive dependencies, analyzes the risk in context of your application, and automatically issues pull requests to help developers keep their code bases secure and compliant.
Prioritize threats based on severity
Leverage comprehensive vulnerability analysis to assess true risks affecting your application, including those powered by AI.
Mend SCA utilizes CVSS 4.0 severity ratings to gauge the potential impact of vulnerabilities affecting your applications and incorporates EPSS exploitability data to assess the likelihood each vulnerability will be exploited.
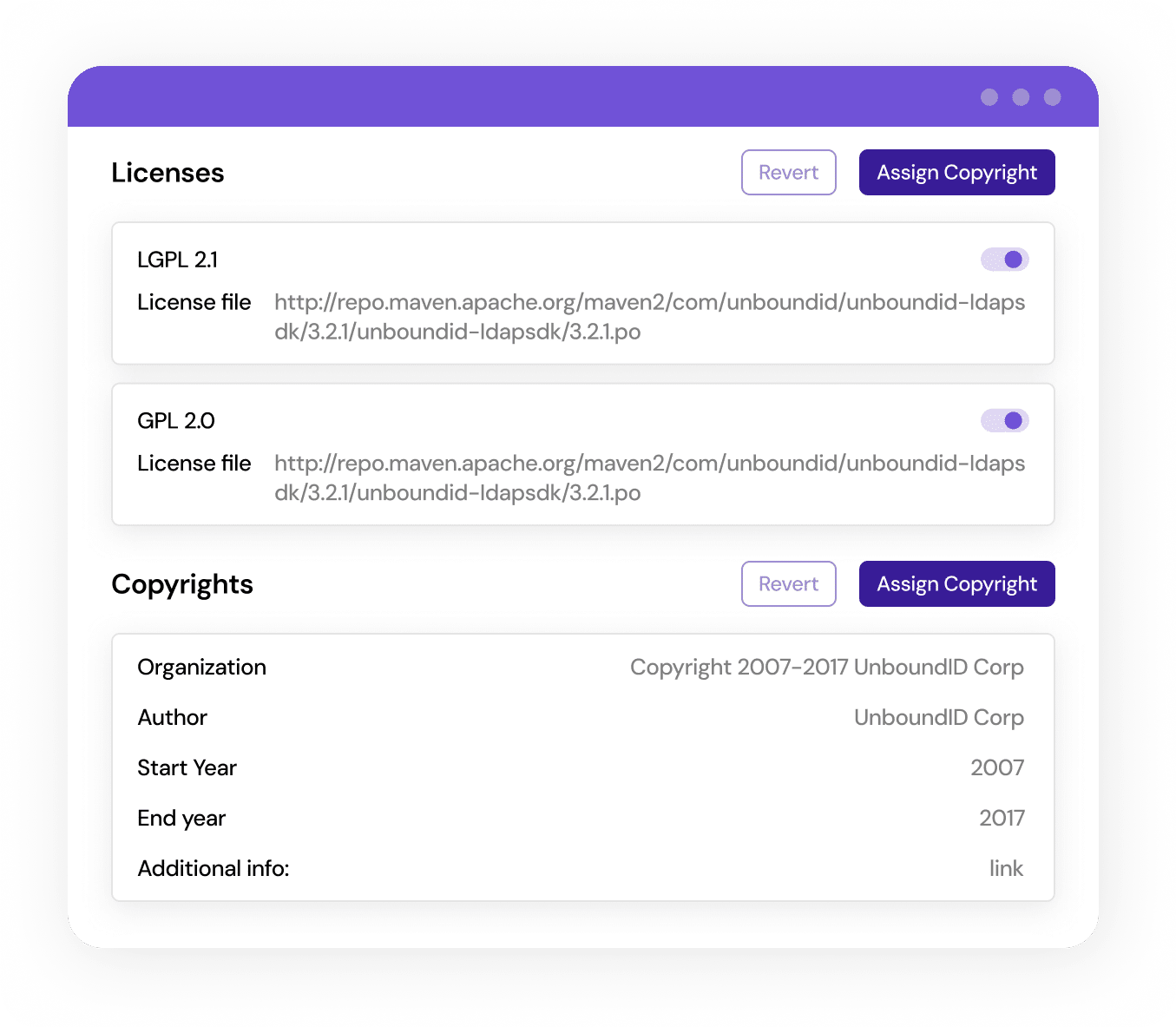
Govern compliance of organizational standards
Give your legal team the visibility and control needed to ensure open source components meet organizational standards as you innovate with AI.
When Mend SCA detects license types that violate company policy, it issues real-time alerts with automatic remediation capabilities and can even block license violations before they become part of your code base.
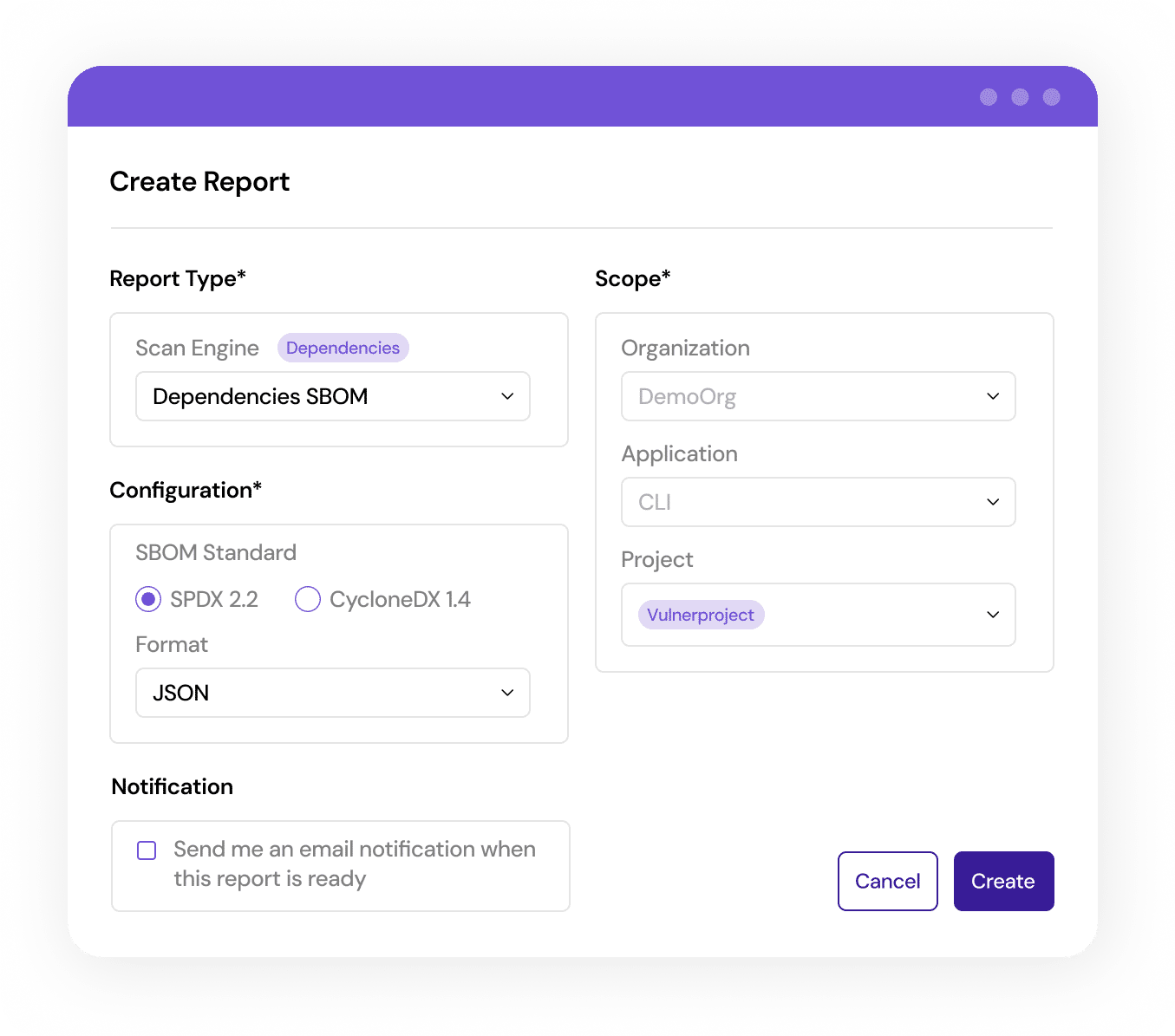
Demonstrate transparency of your supply chain
Mend SCA generates a precise inventory of a software’s open source components, detailing all libraries and dependencies.
Easily export your SBOM in standardized formats (SPDX, CycloneDX) and import third-party SBOMs while leveraging VEX data to meet government and customer requirements with AI transparency.
Frequently asked questions
Where does the vulnerability information come from?
The Mend.io database is the largest and most mature database of open source vulnerabilities. It contains more than 300,000 vulnerable components which are aggregated from the CVE/NVD, and various other sources like the GitHub issue tracker, security advisories, and open source projects issue trackers. Mend.io uses a proprietary patented algorithm that matches between vulnerability and only the impacted version, thus guaranteeing no false positives that waste developers’ time.
How does your SCA product work?
Our plugins integrate with your repositories, build tools, CI servers and more. It calculates the digital signature for all your components without ever scanning your code. It then cross-references the digital signatures with the ones in the Mend.io database to detect the open source components in your products. An immediate up-to-date report is generated with all components and issues detected.
If you have integrated Mend SCA with your build pipeline, the report is generated every time you run your build. If you have integrated Mend SCA with your developers’ repo, Mend SCA detects and displays vulnerabilities immediately when the code is written and/or committed to the repo.
Does Mend SCA include Mend Renovate?
Yes, Mend SCA includes Mend Renovate.
Can you enforce customized policies and how do you enforce it?
Yes, Mend.io enforces policies automatically throughout the software development process. You can define your policies according to security vulnerabilities severity, open source license type, software bugs severity, age of a component and many more. You can approve, reject, initiate an approval flow or open an issue ticket based on your criteria and definitions.
In addition, Mend.io also offers a browser extension, which notifies your developers if a certain component meets your organization’s policies before downloading the component.
What type of reports do you offer?
We offer a variety of reports that will help you monitor all of your open source activity such as an inventory report, due diligence report, high severity bugs report, vulnerability report and many more.
Can I still use your AppSec platform if my environment is not connected to the internet?
Some plug-ins for Mend SCA can be used in isolated environments by generating an update request and saving the request locally as a text file. For these plug-ins, the file can later be moved to an online environment for automatic or manual updates.
Does Mend.io identify risks in both direct and transitive dependencies?
Yes, Mend.io conducts deep scans of open source code to identify risks in direct and transitive dependencies, and produces a compliance report related to standards by NIST
Thanks for requesting a demo.
An account manager will be in contact shortly.
Get started
See how Mend.io can help you proactively manage application risk
Mend offers an enterprise suite of application security tools to help you detect and remediate vulnerabilities in your open source while maintaining full visibility into your entire security risk posture.
Here’s what you can expect after filling out the form:
- Talk to an expert who knows the risks of AI-generated code and embedded AI models
- Get a tailored plan to secure the AI in your apps and your AI generated code
- See how our platform works across your stack: AI, dependencies, containers, and custom code