Advisory: New OpenSSL Critical Security Vulnerability

Table of Contents
November 1, 2022
Update:
OpenSSL released OpenSSL 3.0.7, which patches the following CVEs:
CVE-2022-3786 (OpenSSL advisory) [HIGH severity]
A buffer overrun can be triggered in X.509 certificate verification, specifically in name constraint checking. Note that this occurs after certificate chain signature verification and requires either a CA to have signed a malicious certificate or for an application to continue certificate verification despite failure to construct a path to a trusted issuer. An attacker can craft a malicious email address in a certificate to overflow an arbitrary number of bytes containing the `.’ character (decimal 46) on the stack. This buffer overflow could result in a crash (causing a denial of service). In a TLS client, this can be triggered by connecting to a malicious server. In a TLS server, this can be triggered if the server requests client authentication and a malicious client connects.
CVE-2022-3602 (OpenSSL advisory) [HIGH severity]
A buffer overrun can be triggered in X.509 certificate verification, specifically in name constraint checking. Note that this occurs after certificate chain signature verification and requires either a CA to have signed the malicious certificate or for the application to continue certificate verification despite failure to construct a path to a trusted issuer. An attacker can craft a malicious email address to overflow four attacker-controlled bytes on the stack. This buffer overflow could result in a crash (causing a denial of service) or potentially remote code execution. Many platforms implement stack overflow protections which would mitigate against the risk of remote code execution. The risk may be further mitigated based on stack layout for any given platform/compiler. Pre-announcements of CVE-2022-3602 described this issue as CRITICAL. Further analysis based on some of the mitigating factors described above have led this to be downgraded to HIGH. Users are still encouraged to upgrade to a new version as soon as possible. In a TLS client, this can be triggered by connecting to a malicious server. In a TLS server, this can be triggered if the server requests client authentication and a malicious client connects.
Given the apparent complexity of the attack chain and the presence of other mitigations such as buffer overflow protection in most affected systems, these vulnerabilities are not quite as serious as feared. However, they should still be addressed urgently, and there is little to no risk in upgrading to the fixed version.
October 31, 2022
Last week, the OpenSSL Project announced that on Tuesday, November 1, 2022 1300-1700 (UTC), they will release OpenSSL version 3.0.7 to address a critical CVE.
Here’s what we know:
- The security fix addresses a critical security vulnerability and affects all OpenSSL versions from openssl-3.0.0-alpha1 to openssl-3.0.6. Versions prior to 3.0.0 are not vulnerable.
- According to OpenSSL, an issue rated as critical affects common and likely exploitable configurations. For example, bad actors could exploit the vulnerability to access server memory contents, or remotely access private server keys or other situations where remote code execution is likely to occur.
- Given that roughly two thirds of web servers use OpenSSL, the potential impact of this vulnerability could be significant.
- Affected users should be prepared to immediately update any vulnerable OpenSSL installations when OpenSSL version 3.0.7 is released.
Background on OpenSSL
Most web servers across the internet and intranets alike use SSL certificates to secure connections. These certificates are traditionally generated by OpenSSL – a general purpose cryptography library that enables open-source implementation of SSL and Transport Layer Security (TLS).
The silver lining to this announcement is that OpenSSL version 3 is relatively new and has a somewhat low adoption curve, so the vast majority of users are on the older, unaffected version. However, the newest versions of Linux operating systems such as Ubuntu 22 and Red Hat Enterprise Linux 9 use the vulnerable versions of OpenSSL.
Our security team will add this latest vulnerability to the Mend vulnerability database as soon as more details are available.
What is Mend’s recommended action to fix the OpenSSL vulnerability for my own products?
- Prepare to update any vulnerable OpenSSL installations on Tuesday, November 1, 2022
- Conduct an inventory search within your Mend organization on the OpenSSL libraries affected. This search can be filtered for the affected versions (3.0 – 3.0.6). A report can be generated on your organization’s inventory using the UI and Reports API
Are Mend offerings vulnerable to the OpenSSL vulnerability?
Mend does not use OpenSSL in any of our application code for our offered products, both SCA and SAST. In our cloud infrastructure, we use an older version of OpenSSL prior to v3.0. Therefore, Mend is not impacted by this vulnerability.
Given that the severity is critical, we expect that the attack vector will most likely be “network” (remote attack). Here’s a comparison of attack vector types in terms of overall severity.
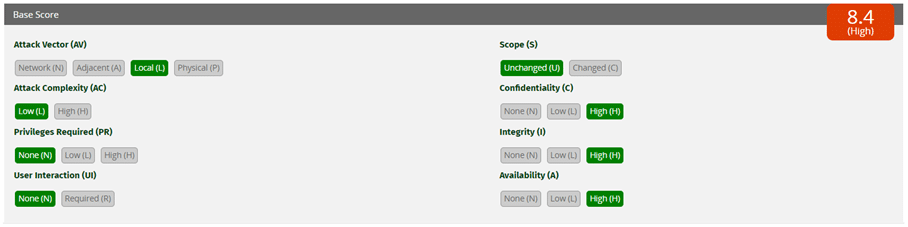
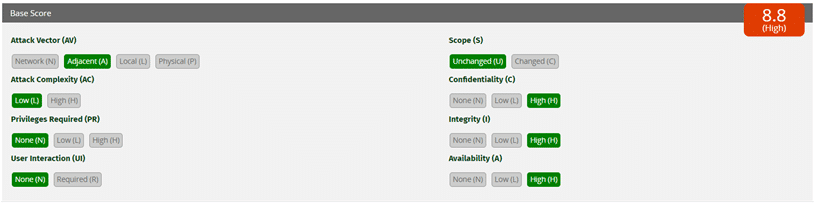
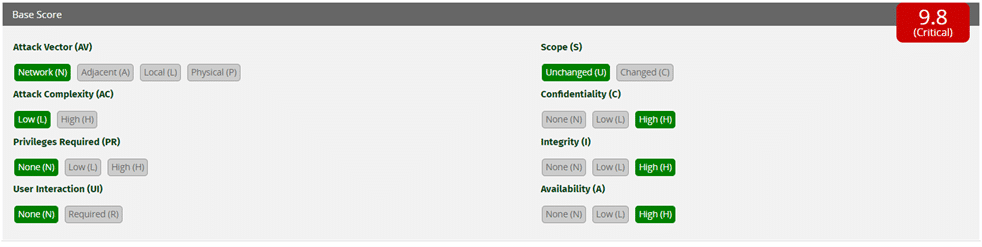
We’re updating our users now on how to remediate any impacted technology and will refresh this blog with further news.


