April Open Source Security Vulnerabilities Snapshot


Oh what a difference a month makes! When we launched our new monthly open source vulnerabilities snapshot series last month, we didn’t imagine that the following post would be researched and written by an unexpectedly remote team.
As we try our best to adjust to this chaotic moment in history, settling into our home offices and turning Zoom into our new watercooler, we find that some things stay the same. Case in point: open source vulnerabilities are on the rise. We’re back with our open source security vulnerabilities snapshot to see what changed and what stayed the same in the open source security ecosystem: how many new open source security vulnerabilities were published in March, what we should look out for, and how the community is addressing them.
Our now-remote research crew dug into the comprehensive Mend database to provide us with all of the information that you need about the new open source security vulnerabilities published in March. The Mend database is continuously updated with new data about open source vulnerabilities, collected automatically from many sources including the National Vulnerability Database (NVD), and other publicly available security advisories and issue trackers in the open source and security communities.
Open Source Security Vulnerabilities Are (Still) on the Rise
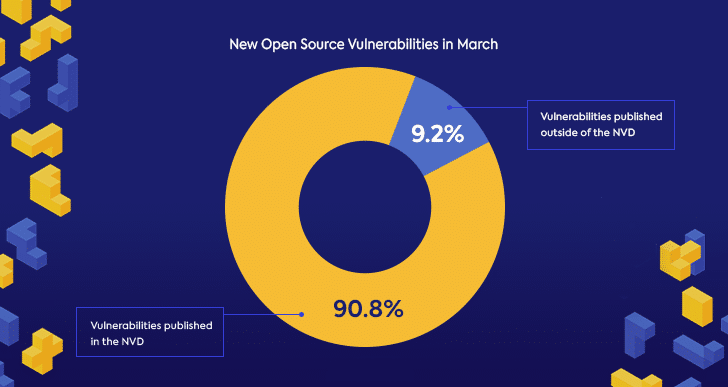
March saw nearly 750 new open source security vulnerabilities published, almost 100 more than in February. It’s worth mentioning that only 90% of these were published in the NVD. The rest were published on open source community and security resources like forums, advisories, and issue-trackers. We saw similar numbers of open source vulnerabilities outside of the NVD in February as well, and when we look at the yearly number of open source vulnerabilities published outside of the NVD, the portion is even larger.
March’s data proves once again that relying exclusively on the NVD for information on open source security vulnerabilities will leave us with some blind spots. The open source community is working hard to comprehensively cover security vulnerabilities in open source projects and make reporting security issues easier for maintainers. Some open source security vulnerabilities are still published on open source resources outside of the NVD.
Open Source Vulnerabilities Severity Breakdown in March
Next, we checked how severity scores were distributed in the new open source vulnerabilities published in March.
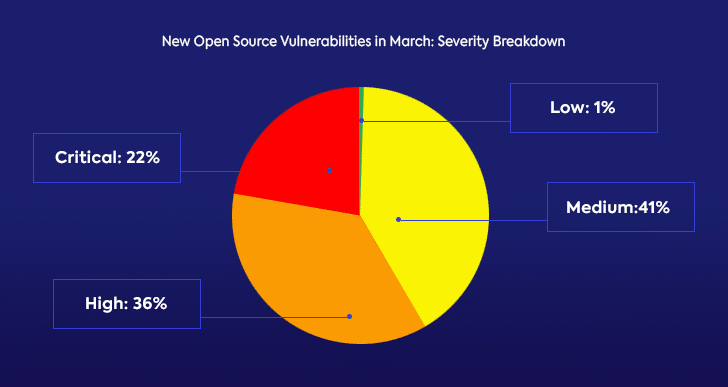
In March, much like the previous month, nearly 60% were either critical or high severity. With the increasingly rising number of security alerts that development teams are required to address, this distribution is particularly concerning. Teams often look to severity scores to prioritize which issues to address first, and if nearly 60% of all open source security vulnerabilities are scored high and critical, addressing them all is a challenge.
The imbalance in the distribution of severity scores has a few possible explanations. In dealing with the continuous rise in the number of vulnerabilities, the security community understandably focuses on the high and critical issues. Another reason behind the high number of high to critical severity vulnerabilities is that creating CVEs can be a time-consuming task that some busy open source project maintainers avoid when it comes for lower-severity issues. It’s important to remember that CVSS does not measure risk, and security and development teams must use additional considerations when prioritizing security vulnerabilities.
Top Open Source CWEs in March
Severity scores are just one aspect of software vulnerabilities. In order to learn more about the new open source security vulnerabilities published in March, we also looked at which types of CWEs were most common.
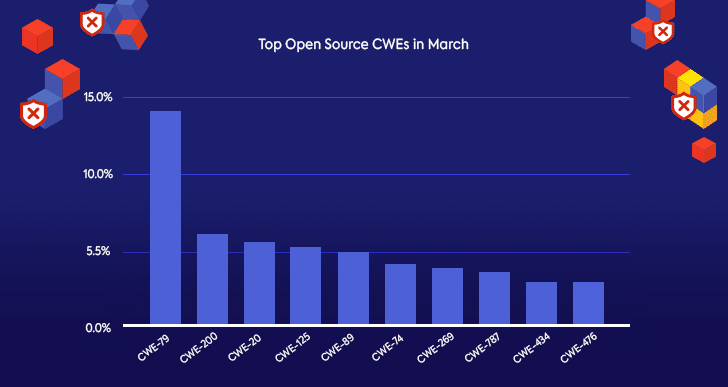
The top three CWEs this month should come as no surprise; they have been the most common for quite a few years. CWE-200 and CWE-20 are both very general issues. As opposed to CWE-79 (XSS), the most common CWE in March that refers to a type of attack, CWE-200 (Exposure of Sensitive Information to an Unauthorized Actor), can relate a large variety of issues and refers to the many consequences of a fairly broad scenario.
CWE-20 (Improper Input Validation) can also be associated with a wide variety of issues, since input validation refers to a wide range of actions that must be implemented in order to ensure security. Since there are so many security measures that need to be put in place, developers often forget to address all of them. In addition, improper input validation can refer to anything from XSS to SQL injection to a number of additional issues, which could all fall under that title.
Programming Languages and New Open Source Vulnerabilities in March
Another interesting aspect that we wanted to look at was how March’s new open source vulnerabilities measured up when it comes to programming languages. We found that the distribution of vulnerabilities per language changed quite a bit.
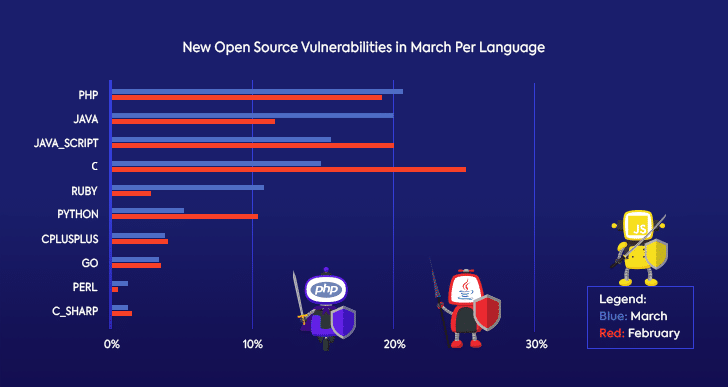
While PHP still holds the dubious distinction of having the most open source vulnerabilities, the rest of the top programming languages saw fairly big rises or falls. The amount of vulnerabilities in Java and Ruby rose substantially since February, while the amount of vulnerabilities in JavaScript, C, and Python saw quite a decrease.
Of course, this doesn’t mean that over the course of a month some languages became more secure while others less so. Some of the reasons might be use of automated tools to discover specific vulnerabilities, or different projects or security researchers doubling down on analyzing a specific project. As the open source community, as well as the software development industry at large, continue to invest time and resources in open source security, these types of spikes in vulnerabilities published per specific project or language are bound to happen. It remains to be seen if any of these changes will become a consistent trend.
Spotlight on FasterXML jackson-databind Serialization Issues
Speaking of a high number of new open source Java vulnerabilities published in March, this month’s spotlight focuses on multiple CVEs published for high and critical serialization issues found in versions of the hugely popular FasterXML jackson-databind, including:
in versions 2.x before 2.9.10.4:
CVE-2019-14892 in versions before 2.9.10, 2.8.11.5 and 2.6.7.3, and
CVE-2019-14893 in all versions before 2.9.10 and 2.10.0
Serialization is considered a very useful mechanism and is widely used. Researcher Shahar Gaziel explains that Java, in particular, encourages developers to use serialization almost everywhere, helping developers to “easily separate the business logic from the IT aspects and scale systems without changing any code.” However, Gaziel warns, serialization can also be used as an effective attack vector.
@cowtowncoder, father of the JSON library explained in a Medium post nearly three years ago that “serialization gadgets” might perform malicious operations as side effects that could allow attacks like remote code execution, denial of service, or expose sensitive data. While results of this exploit could be extremely harmful, @cowtowncode also makes it clear that these types of attacks are not that easy to execute and require many prerequisites.
Since the vulnerable Jackson versions are extremely popular and widely used, we strongly recommend all you Java lovers out there make sure you update to a secure version.
Wash Your Hands of Open Source Security Vulnerabilities
April’s open source vulnerabilities snapshot shows us that when it comes to open source security vulnerabilities management, we all need to stay the course. The number of open source security vulnerabilities went up in March, leaving us with the task of tracking our open source components and making sure that we stay on top of any new vulnerabilities that might come up by updating insecure versions as soon as possible.
While the pandemic has influenced our day to day in many ways, the pace of software production has not slowed down. If anything, we are more dependent on software than ever, and that software consists mostly of open source libraries. Making sure that we have all of the open source security tools and policies that we need throughout the DevOps pipeline is essential to make sure that the software products and services that we use and create are as safe as possible.
Want to learn more about March’s top open source security vulnerabilities? Check out Mend’s Vulnerability Lab!

