What Role Should Dependency Management Play as the Regulation of the Software Supply Chain Escalates?

Two big trends are now converging that will change the way we view and implement software supply chain security and make dependency management a vital part of assuring security. Let’s look at why and how this is happening, and what it means for dependency management.
Why has the landscape changed in the software supply chain?
First, more software and applications are being developed than ever before, with ever more complex chains of components and dependencies that have led to a rise in vulnerabilities and an increased threat of malicious packages. To demonstrate this, the Mend Open Source Risk Report recorded a 33 percent growth in the number of open source software vulnerabilities added to the Mend.io vulnerability database in 2022, which outstripped the estimated 25 percent growth in the amount of open source software available. And Mend Supply Chain Defender showed a steady quarterly increase in the number of malicious packages published in 2022, with a significant jump in Q3, which increased 79 percent from Q2.
In turn, this has caught the attention of governments across the world from, the U.S. and the EU, to as far afield as Australia and New Zealand, leading to the second big trend, which is the introduction of governmental cybersecurity strategies and a recognition that regulation of the software supply chain is necessary to protect security on national, economic, public and private levels.
Why is dependency management important for securing the software supply chain?
Simply put, you can only protect your software and applications, identify issues, and then fix them if you know the following:
- What components and dependencies are in your software and applications
- Whether they are up-to-date and properly patched
- Whether open source third-party components and dependencies are compliant with the terms and conditions of their use
- Whether these components and dependencies are behaving as expected or are operating unusually
- If any others are being adversely affected
- What components and dependencies should and shouldn’t be there
Dependency management gives you the visibility you need to answer these questions and the capability to address any issues that you detect as a result. It involves identifying all dependencies used in your software, regularly monitoring and updating dependencies to ensure they are not vulnerable to known security issues, and maintaining a list of approved and unapproved dependencies.
How will escalating regulation affect the role of application dependency management?
More regulation means more accountability. More accountability requires increased visibility into the supply chain, comprehensive disclosure of components, dependencies, and any flaws and malicious packages that could threaten the stability and security of the software. So, the ability to catalog every component and dependency, identify threats and remediate them through a process of dependency management, becomes necessary.
With more stringent regulation and governance likely to be implemented, the transparency of software supply chain constituents becomes essential. Spearheaded by the likes of the U.S. Cybersecurity and Infrastructure Security Agency (CISA) and the Five Eyes Alliance, government cybersecurity strategies will require any company working with federal, public, national, and international organizations to disclose all the components and dependencies in their software, applications and code bases. These strategies shift the responsibility to vendors, to both infuse security into their platforms and to declare any threats and vulnerabilities that they encounter. What has until now been voluntary best practice will become pre-requisites, and what begins with large public contracts will inevitably spread to the private sector, as vendors to federal and public bodies will demand that their suppliers in turn undertake the same level of due diligence.
What tools do you need to manage application dependencies effectively?
Effective dependency management involves the implementation of a prophylactic strategy that should include a combination of identification, detection, prioritization, updates and remediation.
Identification lies at the core of the regulations and strategies proposed by governmental agencies. It is the key to cataloging and knowing what components and dependencies exist within your software and applications, and it’s the foundation for accountability and transparency. You achieve this by using a software bill of materials (SBOM) and making it available to all your customers. The SBOM will not only provide comprehensive visibility into your code base, but it will improve your ability to detect anomalies, flaws, and vulnerabilities in your code which could be a threat. As a result, using an SBOM can reduce your time to respond and remediate any issues. As such, we anticipate that the SBOM will become a prerequisite tool for effective dependency management.
Having identified and detected any vulnerabilities, you need to update and patch your software regularly, frequently and in a timely manner, to ensure that it’s resistant to newly arising issues and attacks. First, you’ll need to employ a tool that prioritizes which vulnerabilities are most critical and should be addressed first. Prioritization optimizes the updating and remediation process, ensuring that you address dependencies that are most important to your code base, so that you don’t waste time on those that are unimportant or redundant.
Then you can move on to actively updating your dependencies, and you can do this most effectively with a tool that automatically applies updates when they are identified. Additionally, you can apply automated remediation to vulnerabilities that need to be fixed, using software composition analysis (SCA) for open source dependencies and static application security testing (SAST) for custom code. Automation slashes mean time to remediation, thereby making your dependency management as efficient as possible. Couple these tactics with a tool that prevents malicious open source packages from entering your codebase and the capability to apply governance and compliance policies, will redouble your security and your dependency management.
Ideally, all of these capabilities should be rolled into one comprehensive platform that brings all these processes together in a security package that operates seamlessly with your development workflow, maximizing security without sacrificing development speed or efficiency.
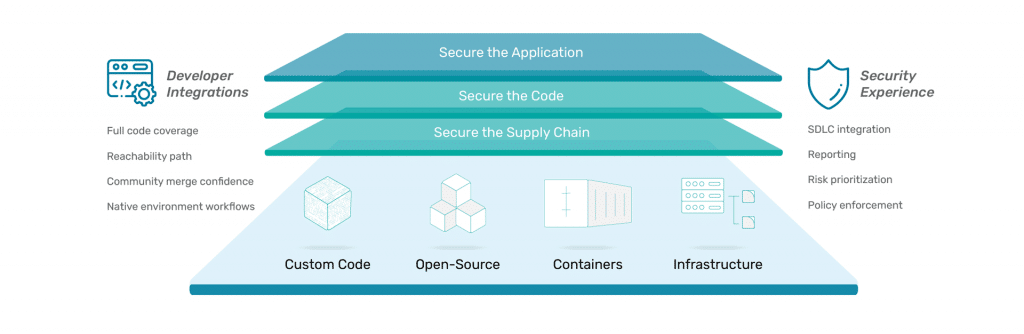
That’s how you can ensure that dependency management plays the most effective role in securing your code base and meeting the requirements of increased due diligence that comes with more regulation and governance of the software supply chain.
