Application Security Testing: Security Scanning Vs. Runtime Protection

Table of Contents
The application layer continues to be the most attacked and hardest to defend in the enterprise software stack. With the proliferation of tools aimed at preventing an attack, it’s no wonder the application security testing (AST) market is valued at US 4.48 billion. Forrester’s market taxonomy breaks up the application security testing tools market into two main categories: security scanning tools and runtime protection tools.
Security scanning tools are used to remediate vulnerabilities while applications are still in development. Runtime protection occurs when applications are in production and are considered an extra layer of protection, not an alternative to scanning.
In this blog, we’ll define four security scanning tools and three runtime protection technologies, looking at the pros and cons of each.
Security scanning tools
Security scanning tools are used primarily in development with applications being tested as they are designed and built. The goal of security scanning tools is prevention. These tools identify and remediate vulnerabilities in applications before they run in a production environment. Tools in this market include SAST, DAST, IAST, and SCA.
Static Application Security Testing (SAST)
Static application security testing (SAST) is white-box testing, where source code is analyzed from the inside out while components are at rest. SAST analyzes application source code, byte code, and binaries for coding and design flaws that suggest possible security vulnerabilities.
The most mature of all application security testing tools, SAST scans code at rest and is usually implemented during development and QA. Often it is integrated into CI servers and integrated development environments (IDEs).
With SAST, scans are based on a set of predetermined rules that define the coding errors in the source code that need to be assessed. SAST scans can be designed to identify some of the most common security vulnerabilities, including SQL injection, input validation, and stack buffer overflows.
Dynamic Application Security Testing (DAST)
Dynamic application security testing (DAST) is black-box testing that looks for security vulnerabilities and architectural weaknesses by simulating external attacks on an application while the application is running. It attempts to penetrate an application from the outside by checking its exposed interfaces for vulnerabilities and flaws. As such, it has no access to source code and is able to uncover vulnerabilities only through external attacks.
The dynamic part of DAST’s name comes from the test being performed in a dynamic environment. Unlike SAST, which scans an application’s code line by line when the application is at rest, DAST testing is executed while the application is running. While DAST can be used in production, testing usually is carried out in a QA environment.
Interactive Application Security Testing (IAST)
Interactive application security testing (IAST) scans an application’s source code post-build in a dynamic environment. Testing occurs in real time while the application is running, usually in a QA or test environment. Because IAST is analyzing source code, testing is able to identify the problematic line of code and notify the developer for immediate remediation.
Although both SAST and IAST look directly at code, IAST does so post-build in a dynamic environment through the instrumentation of the code. Agents and sensors are deployed in the application, analyzing code to identify vulnerabilities. IAST can be easily integrated into the CI/CD pipeline, is highly scalable, and can be either automated or performed by a human tester.
Software Composition Analysis (SCA)
Software composition analysis (SCA) tools perform automated scans of an application’s code base to provide visibility into open source software usage. This includes identifying all open source components, their license compliance data, and security vulnerabilities. In addition to providing visibility into open source software use, SCA tools also prioritize open source vulnerabilities and ideally provide insights and auto remediation to resolve security threats.
Runtime protection tools
Runtime protection tools are designed to ward off attacks while an application is running in a production environment. These tools react in real time to defend against malicious agents. This market is segmented into web application firewalls (WAF), bot management, and runtime application self-protection (RASP).
Web Application Firewall (WAF)
Web application firewalls (WAFs) filter, monitor, and block HTTP traffic to and from web applications, protecting against a variety of common application layer attacks such as cross-site scripting (XSS) and SQL injection. In essence, a WAF stands in front of a web application acting as a shield between the application and the internet. Unlike regular firewalls that act as a safety gate between servers, WAFs filter the content of specific web applications to thwart malicious attacks in real time.
WAFs operate through policies that protect against vulnerabilities in an application by filtering out malicious traffic. Policies can be quickly and easily modified to respond to differing attack vectors. For example, rate limiting can be implemented during a DDoS attack.
Bot Management
A bot manager is software that manages bots by distinguishing between good bots and bad bots instead of simply blocking all non-human traffic. A good bot manager should be able to identify a bot’s reputation and block bots based on their IP address reputation. By analyzing bot behavior, a bot manager should be able to add good bots like Google’s Site Crawlers, which index web pages, to allowlists, while challenging bad bots using methods like a Captcha test or JavaScript injection. Bot managers can limit bots over-using a service or deny access to certain content or resources for bots identified as bad.
Runtime Application Self-Protection (RASP)
Runtime application self-protection (RASP) is a security technology capable of controlling application execution and is designed to detect and prevent attacks on applications in real time from the inside. RASP prevents attacks automatically with no human intervention by “self-protecting” or reconfiguring in response to malicious input or behavior. It does this by analyzing the context of suspected malicious behavior and by continuously monitoring its own behavior to automatically detect and mitigate attacks.
RASP monitors and protects applications against a range of threats, such as SQL/command injections, cross-site scripting (XSS), data exfiltration, and account takeovers.
Application security testing: No one tool can do it all
The truth is, in today’s threat landscape, no one tool can do it all. Organizations need multiple tools from this list to secure their applications and minimize their risk. To help you understand the pros and cons of each of these tools, we’ve compiled a list of features and functions, showing how each tool stacks up against each other in terms of coverage, accuracy, and more.
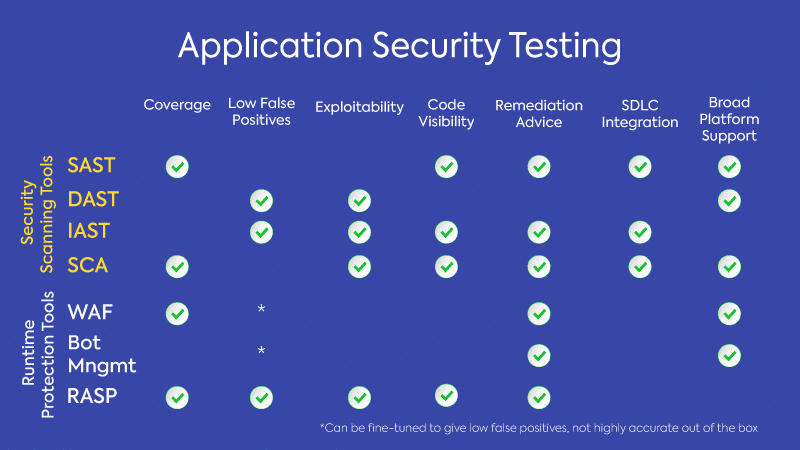
By using a combination of these tools, you can reduce your overall security risk. Remember that there is no one perfect solution. Besides, in security where threats are constantly evolving, perfect can be the enemy of good.


