Securing the Software Supply Chain: Key Findings from the Mend Open Source Risk Report


Threat actors will always target the things most important to businesses, and today, that means applications–the lifeblood of the global economy. As the recent Mend Open Source Risk Report reveals, the ongoing rise in open source vulnerabilities and software supply chain attacks presents significant business risk. The number of open source vulnerabilities are growing, just as threat actors are launching increasingly sophisticated attacks.
In a recent webinar, Jeffrey Martin, vice president of outbound product management at Mend, discussed the key findings from the report.
Rising vulnerabilities
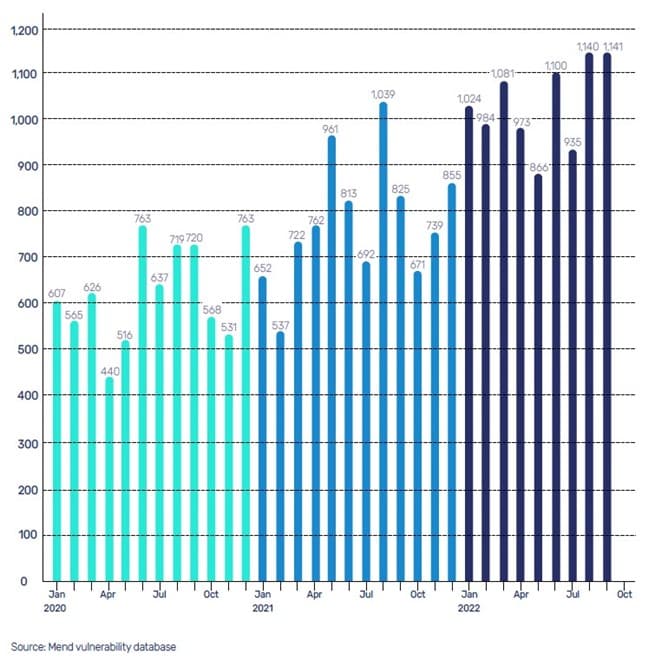
The report data show that the percentage of open source vulnerabilities grew from 25 percent in 2021 to 33 percent in 2022.

There are several reasons for that. “More open source code is now being produced, and thanks to automation tools, more vulnerabilities are discovered,” Martin said. “Consequently, more open source vulnerabilities get reported.”
And while vulnerability growth may fluctuate short term, “The fact is, there are always more vulnerabilities to disclose. It’s getting to the point where it’s impossible to manage them all, with a thousand or so dropping every month,” he said.
Battling the remediation gap
The report analyzed how long respondents took to fix vulnerabilities and what percentage they were fixing. “We found that only 13 percent of vulnerabilities were getting fixed, and on average it takes 271 days to fix a vulnerability,” Martin said. That leaves a serious security hole because it’s taking three-quarters of a year to fix a known vulnerability.
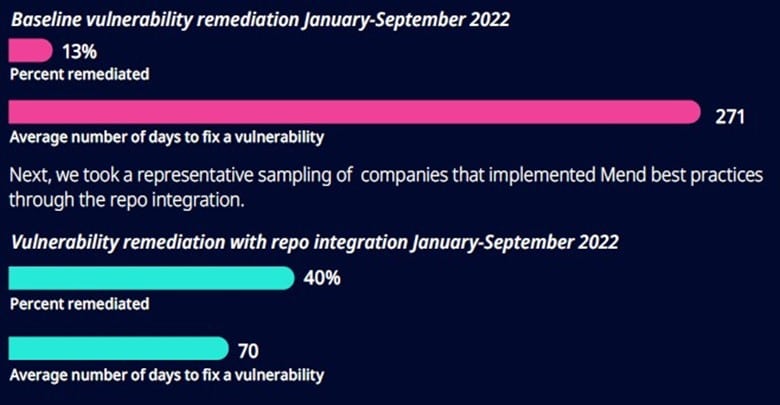
However, those respondents who remediated vulnerabilities using repo integration saw a much higher rate of remediation in a much shorter time. “That means there’s a smaller window of opportunity for attackers to exploit vulnerabilities, and you’re reducing risk,” Martin said. ”Interestingly, the average number of days to fix a vulnerability isn’t a nice clean average at 70. Lots of people are doing it instantly, by creating a pull request and clicking “merge” immediately.”
Handling functional risk
Martin also noted the issue involved in balancing security risk with functional risk. While application security is of foundational importance for business applications, so is the need to keep them functional, and companies sometimes find it difficult to achieve equilibrium.
“This issue arises as a result of aging components, which become harder to update. You then have to make trade-offs to remediate the vulnerability and fix all the functional problems,” Martin said. A lack of granular information can also make it difficult to see what functional risk is being introduced. Companies need to know not just whether or not there’s a vulnerability and a fix inside of a given version, but also what the consequences are of moving to that version, including functional risks, additional security risks, and whether they can confidently accept and merge a pull request.
“One of the reasons vulnerability remediation is more effective with Mend is that we provide a Merge Confidence score that tells you how recent the update was and whether other people who have already adopted the change have had problems,” Martin said.
Malicious packages
According to data from Mend Supply Chain Defender, increasing amounts of malicious packages have been introduced over the past year. “In a given month, there can be two to three thousand malicious packages published,” Martin said. “And most of them look like something else, that’s valuable and safe.”
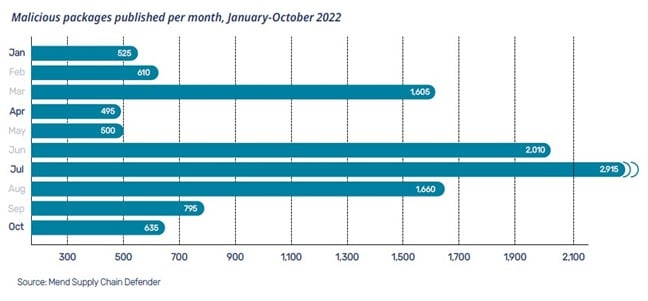
Attackers are also deploying more sophisticated techniques. More packages contain telemetry, which enables data collection, and some are now built more deeply within the software supply chain, such as when valid content has a dependency containing malicious code.
There have also been several cases of trusted packages suddenly becoming malicious, when a new commit makes them unsafe. These packages won’t be identified as new, so they won’t raise suspicions.
Malicious package attack vectors
There are four basic attack vectors for malicious packages: brandjacking, typosquatting, dependency hijacking, and dependency confusion. Typosquatting is a favorite, although it isn’t quite as effective as it used to be. Brandjacking is growing, while dependency hijacking and dependency confusion are newer vectors.
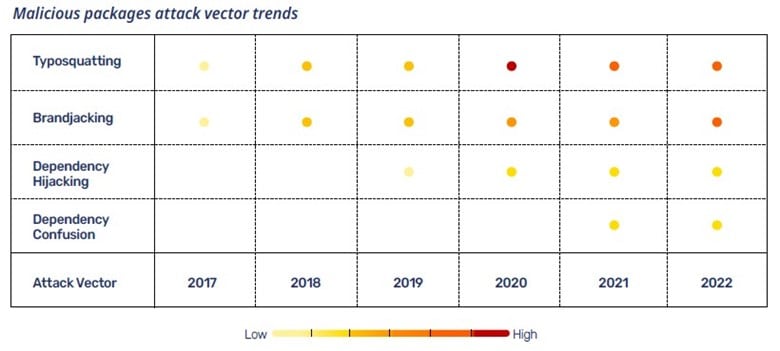
“It’s important to note that the older types aren’t going away,” Martin said. “It’s just that malicious actors are finding new ways to complement their more established methods.”
The key lesson
Everything is software and application-driven these days. Bad actors know this, so threats continue to multiply and grow in sophistication. And as threat landscape activity continues to increase in volume and innovation, enterprises need to move beyond today’s status quo in order to survive. Enterprises’ application security falls behind when they can’t keep pace with the growth in threats, Martin noted. “Effective security requires companies to leverage prioritization and remediation tools and processes that target the vulnerabilities which will most impact your systems and your business,” he said.
