Setting Up an Effective Vulnerability Management Policy


Considering the continuous increase in cybersecurity attacks targeting large organizations over the past few years and regulations like PCI DSS, HIPAA, NIST 800-731 – to name a few – it’s no surprise that enterprise investment in vulnerability management is on the rise.
Detecting, prioritizing, and remediating security vulnerabilities in today’s rapidly evolving threat landscape is no small feat. A comprehensive vulnerability management policy has become imperative for companies that are dedicated to minimizing security risk. This requires a strategy that will enable teams to implement a continuous vulnerability management process that increases their visibility over threats and allows swift remediation when needed.
What is a vulnerability management policy?
The ISO 27002 standard defines a vulnerability as a “weakness of an asset or group of assets that can be exploited by one or more threats.” While ISO and other standards have required organizations to implement a vulnerability management policy for quite some time, the security ecosystem continues to evolve, demanding organizations update their vulnerability management approach. This includes everything from the attack surfaces they are required to address to the processes and tools they implement, not to mention the parties responsible for different parts of an organizational vulnerability management policy.
Security scans can no longer be a periodic occurrence – they must be run continuously, enabled by automated tools. In order to address the increased security debt that most organizations are experiencing due to the rising number of vulnerabilities, a prioritization and remediation strategy must be implemented. In addition, security, development, and DevOps teams must all take part in the vulnerability management efforts in order to ensure threats are mitigated swiftly and efficiently. All of these moving parts must be detailed clearly as part of a comprehensive vulnerability management policy.
The scope of a vulnerability management policy
While the scope of a policy may vary depending on the size, type, and industry of an organization, a vulnerability management policy typically covers network infrastructure; servers; operating systems; virtual machines; cloud-hosted servers; database servers; databases; proprietary, third-party, and open source applications; company-owned devices; and more. It’s important to map out the scope and document it clearly to help avoid any uncertainty as to what is being monitored and how.
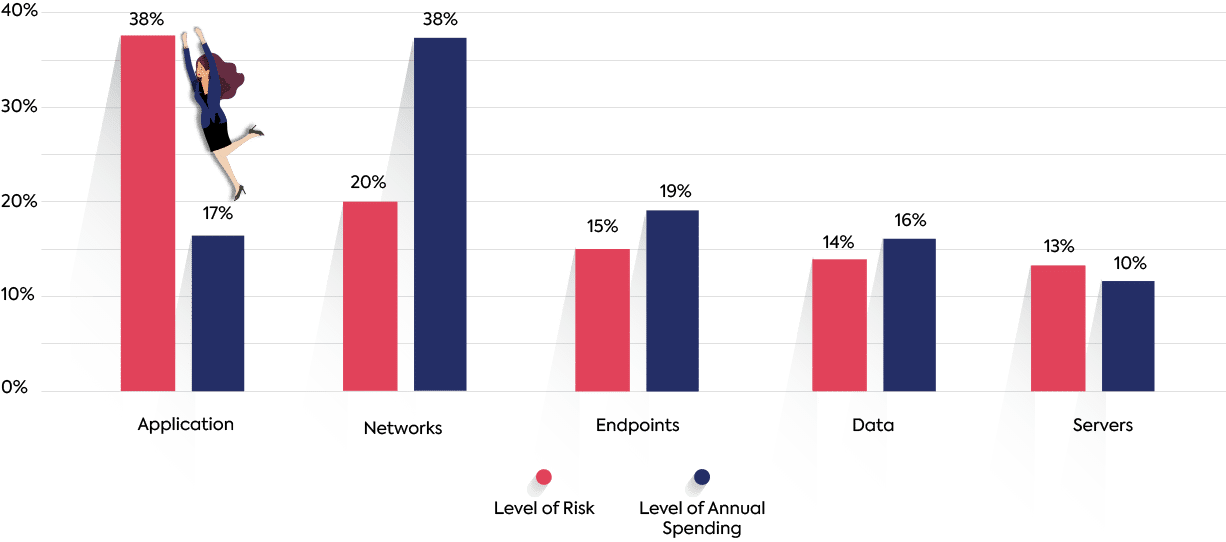
It’s also important to remember that each of the devices, environments, and frameworks that comprise an organizations’ system present a different type of risk. A recent research report from Ponemon Institute analyzed IT Security spend trends and found considerable gaps between the perceived level of risk for some of the attack vectors and the level of annual spending for the different protection layers. An effective vulnerability management policy will properly address each type of security threat and ensure that the right processes and tools are put in place to address the level of risk introduced by different vectors and layers.
Vulnerability management policies: Roles and responsibilities
The roles and responsibilities in a vulnerability management policy have also undergone a change over the past few years. As threat landscapes evolved and release cycles sped up, the shift left approach and the DevSecOps movement introduced an updated organizational culture where security, development, and DevOps teams share ownership of vulnerability management.
Vulnerability management is no longer solely in the hands of the security team, performed toward the end of a development cycle. Vulnerability detection and remediation are also addressed by developers at the earliest stages of the SDLC.
In today’s enterprise environments, where team members work remotely around the globe, a vulnerability management policy helps ensure that all teams across the organization are aligned on the processes and strategies in place.
How to implement a vulnerability management policy
Every vulnerability management policy, no matter the size of the organization, requires organizations put four steps in place: identification, evaluation, remediation, and reporting.
Step 1: Identification
In the identification stage, teams must scan all devices and environments to detect vulnerabilities. This requires a number of automated scanning tools for the various IT environments and phases of the DevOps pipeline.
Step 2: Evaluation
In this stage, the discovered vulnerabilities are analyzed and assessed to rule out false positives and identify the issues that pose the most risk to your organization.
Step 3: Remediation
Prioritization is a crucial part of this step. As organizations amass security debt and teams struggle to deal with alert fatigue, it’s important to set up a vulnerability prioritization strategy to ensure that remediation efforts are invested in the most immediate security threats, rather than wasted on addressing a laundry list of vulnerabilities with varying risk levels.
Step 4: Reporting
In order to ensure that your vulnerability management policy is working, and fix the parts that need improvement, not to mention remain compliant, reporting is an essential part of the process. Reporting also helps create and track KPIs for teams to ensure that their vulnerability management processes are effective and improve them when needed.
Once all of these stages are streamlined, the vulnerability management policy can provide organizations with a comprehensive and clear framework and process for vulnerability management.
