Table of contents
Infrastructure as Code: How It Works & Top Tools in 2025
Modern development teams move too fast for manual infrastructure management. Infrastructure as Code (IaC) bridges that gap by treating servers, networks, and configurations as software—automated, versioned, and deployed with the same precision as application code. This shift has transformed DevOps from a manual craft into an auditable, scalable system.
This article is part of a series of articles about Application Security testing.
What is Infrastructure as Code?
Infrastructure as Code (IaC) manages and provisions data center infrastructure (servers, databases, networks) using code and configuration files, replacing manual processes and enabling automation, consistency, and speed in software development and operations. IaC reduces costs, improves reliability, and enhances collaboration by treating infrastructure like application code, which can be versioned, tested, and deployed using CI/CD pipelines.
How it works:
- Configuration files: You define your infrastructure, such as the required number of servers, their configurations, and network settings, in plain text files.
- Automation tools: These configuration files are read by software tools that automatically create and manage the infrastructure based on the defined code. Popular tools include Terraform, Ansible, Chef, and AWS Cloudformation.
- Version control: The code can be stored in a version control system (like Git) alongside your application code, allowing for tracking changes, collaboration, and rollbacks.
- CI/CD integration: IaC integrates with Continuous Integration and Continuous Deployment (CI/CD) pipelines to automate infrastructure provisioning as part of the software development workflow.
- Consistency: The system ensures that code is consistent across dev, testing, and production environments.
- Scalability: You can more easily scale the infrastructure up or down by editing and redeploying the code.
Key benefits of IaC include:
- Automation and speed: Automates complex infrastructure setups, drastically reducing the time it takes to deploy and manage environments.
- Consistency and reliability: Ensures consistent environments across development, testing, and production, minimizing configuration drift and errors.
- Reduced costs: Eliminates manual effort, which lowers labor costs and allows teams to focus on other tasks.
- Improved collaboration: Treats infrastructure as code, which can be shared, versioned, and reviewed, fostering better collaboration between development and operations teams.
- Enhanced security: Enables security checks and guardrails to be built into the code, preventing vulnerable configurations from reaching production—especially when paired with modern application security testing tools.
How does Infrastructure as Code work?
Infrastructure as code works by defining infrastructure configurations in human-readable code files, typically using declarative or imperative syntax. These configurations are then interpreted by IaC tools, which provision and manage the required infrastructure resources automatically.
Declarative vs. imperative approaches
- Declarative IaC specifies what the desired state of the infrastructure should be. The tool figures out the steps to reach that state. Examples include Terraform and AWS CloudFormation.
- Imperative IaC describes how to achieve the desired infrastructure setup, step by step. Tools like Ansible and Chef often follow this approach.
Key components
- Configuration files: IaC uses configuration files (often in formats like JSON or YAML) to describe the desired state of the infrastructure.
- Automation tools: IaC automates the provisioning and management of infrastructure, reducing manual effort and errors.
- Version control: IaC integrates with version control systems (like Git), allowing for tracking changes, collaboration, and rollbacks.
- CI/CD integration: IaC works with Continuous Integration and Delivery pipelines to ensure code is automatically provisioned throughout the software development lifecycle, enabling consistent environments for black box testing of running services.
Workflow example
- A developer writes infrastructure definitions in a config file.
- The file is committed to a version-controlled repository.
- A CI/CD pipeline triggers the IaC tool to apply the configuration.
- The cloud environment is provisioned or updated based on the defined state.
This process ensures that infrastructure changes are repeatable, testable, and traceable, aligning development and operations under a unified, automated workflow—and makes it easier to deploy instrumented builds for interactive application security testing (IAST).
Immutable infrastructure vs. mutable infrastructure
Immutable infrastructure refers to a paradigm where components, once deployed, are never modified. Any updates require a new version of the component to be created and deployed, replacing the old one. This approach ensures consistency and eliminates configuration drift, as every change results in a clean, predictable environment.
Mutable infrastructure allows updates to be made to existing components after deployment. While this approach can be more flexible and faster for small changes, it increases the risk of inconsistencies across environments and makes debugging more difficult due to unpredictable state changes over time.
With IaC, immutable infrastructure is often preferred, as it aligns with the practice of treating infrastructure definitions as version-controlled code. It facilitates safer rollbacks, clearer change histories, and more reproducible environments, especially in CI/CD pipelines. However, certain operational tasks or legacy systems may still require mutable strategies, so teams must choose based on their use case.
What is the role of IaC in DevOps?
Infrastructure as code plays a central role in DevOps by bridging the gap between software development and IT operations through automation, collaboration, and consistency. It allows teams to manage infrastructure in the same way they manage application code, using practices like version control, peer review, and automated testing:
- Enabling continuous delivery: IaC allows infrastructure to be provisioned and configured automatically as part of the CI/CD pipeline. T
his means environments can be spun up and torn down quickly and reliably for testing, staging, or production—ideal for repeatable Dynamic Application Security Testing (DAST) runs—enabling faster and more frequent deployments without manual intervention. - Reducing configuration drift: By enforcing consistent, versioned infrastructure configurations, IaC helps prevent configuration drift — a common problem in environments that are updated manually. With IaC, every change is documented and reproducible, making environments more stable and reducing bugs caused by inconsistencies.
- Supporting collaboration and transparency: Storing infrastructure code in shared version control systems (like Git) fosters collaboration between developers and operations teams and supports “shift-left” practices like white box testing during review. Changes are transparent, auditable, and traceable, enabling better teamwork and simplifying reviews and audits.
- Enhancing disaster recovery and scaling: IaC scripts can be reused to rebuild infrastructure in a disaster recovery scenario or to replicate environments for scaling across regions or availability zones. This ensures business continuity and supports growth without the complexity of manual configurations.
- Promoting shift-left practices: With IaC, infrastructure provisioning becomes part of the early stages of development. Developers can create and test infrastructure alongside application code—combining internal insight with external validation in a greybox testing style—identify issues sooner, and deploy more confidently, aligning with shift-left principles in DevOps.
Infrastructure as Code security
While IaC boosts efficiency overall, it can also amplify mistakes. By moving so quickly, a minor error by a DevOps admin at the template level can be propagated across an organization’s entire cloud infrastructure. For this reason, IaC security must be implemented to reduce cloud security risk.
IaC security solutions vary from traditional Appsec testing tools to managing policies and IaC templates. Because developers far outnumber security professionals, security needs to be shifted left to as early in the development life cycle as possible.
Developers need an IaC security solution that allows them to consistently apply security best practices across the SDLC to reduce potential security misconfigurations and vulnerabilities from being deployed to production environments.
IaC security should also encompass who is and who is not allowed to run scripts as well as limiting the permissions of IaC users. The principle of least privilege, in which users are given the absolute minimum levels of access required to perform their job functions, applies here and is an important part of IaC. In production, runtime application self-protection (RASP) complements IaC guardrails by detecting and blocking attacks inside the running application.
Notable IaC tools
1. Terraform

Terraform is an open-source infrastructure as code (IaC) tool developed by HashiCorp that enables users to define, provision, and manage infrastructure across a wide range of cloud providers and services using human-readable configuration files. It supports cloud and on-premises environments, offering a consistent workflow that automates the lifecycle of infrastructure components.
Key features include:
- Multi-provider support: Works with a wide array of platforms via official and community-built providers available in the Terraform Registry (e.g., AWS, Azure, GCP, Kubernetes, GitHub).
- Declarative configuration: Uses configuration files to define end-state infrastructure without the need to specify step-by-step operations.
- Execution planning: Generates a detailed plan showing what changes will be made before applying them, improving transparency and reducing risk.
- State management: Maintains a state file that serves as the single source of truth, helping Terraform track current resource states and manage updates accurately.
- Dependency management: Builds a dependency graph to determine the correct order for provisioning and modifying resources, executing non-dependent actions in parallel to speed up deployments.
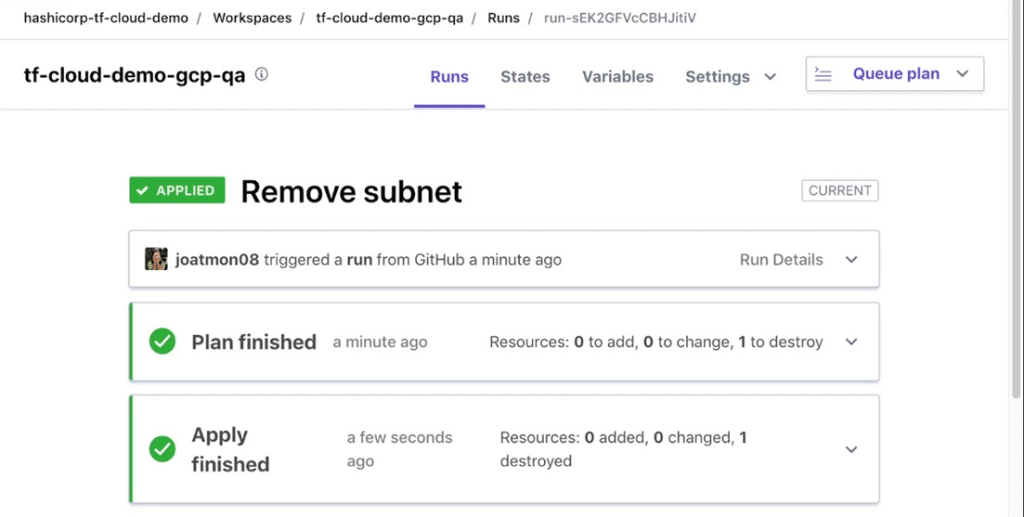
Source: Terraform
2. Ansible

Ansible is an open-source automation tool used to configure systems, deploy applications, and orchestrate IT tasks across environments. Written in Python, it uses a human-readable language (YAML) to define automation tasks in files called playbooks. It operates without agents, relying instead on standard protocols like SSH to connect to managed nodes.
Key features include:
- Agentless architecture: No agents need to be installed on managed nodes. Ansible uses SSH (or WinRM for Windows) to connect and push configuration tasks.
- Modular execution: Sends small programs (modules) to target systems, executes them to bring systems to the desired state, and removes them afterward. Modules are designed to be idempotent, meaning they only make changes when necessary.
- Simple inventory management: Uses plain-text INI or YAML files to define hosts and groups. Can also pull dynamic inventory data from cloud providers like AWS, Azure, and GCP.
- Playbooks and YAML syntax: Uses YAML to write playbooks that define tasks and roles. This makes it readable and easy to learn for new users without deep programming experience.
- Flexible authentication: Supports a variety of authentication methods, including SSH keys, Kerberos, LDAP, and integration with secrets management systems like Ansible Vault, HashiCorp Vault, and Azure Key Vault.
Source: Ansible
3. Chef

Chef (Progress Chef) is a DevOps platform for configuring, deploying, and managing application infrastructure with security and compliance controls. It supports cloud-to-edge operations and includes Chef Courier for job orchestration.
Key features include:
- Cloud-to-edge management: Configure, deploy, and manage application infrastructure consistently across clouds and edge environments, emphasizing security and compliance throughout the lifecycle.
- Configuration at scale: Manage configuration changes at cloud scale to maintain consistency and control across large estates without relying on ad-hoc processes.
- Cloud-native asset security: Secure cloud-native assets on any cloud, applying consistent policies to reduce misconfigurations and improve posture across heterogeneous environments.
- Compliance management: Shift from configuration management to compliance management, enabling repeatable controls and push-button compliance audits for regulated environments.
- Edge delivery and orchestration: Optimize application delivery on edge devices and orchestrate jobs with Chef Courier to simplify enterprise job management across locations.
Source: Chef
4. AWS CloudFormation

AWS CloudFormation is a managed service that automates the provisioning and configuration of AWS infrastructure using templates written in JSON or YAML. Instead of manually creating and linking individual AWS resources, users define the desired state of their environment in a single declarative template, and CloudFormation handles the creation and configuration of resources.
Key features include:
- Declarative templates: Define infrastructure resources such as EC2 instances, RDS databases, VPCs, and load balancers in a single template, using YAML or JSON.
- Stack-based deployment: Group related resources into a “stack” that can be deployed, updated, or deleted as a unit, simplifying lifecycle management.
- Automated dependency management: Automatically determines and respects resource dependencies, ensuring resources are created in the correct order without manual intervention.
- Repeatable deployments: Reuse templates across regions and accounts to replicate infrastructure consistently, supporting high availability and disaster recovery strategies.
- Change sets: Preview the impact of a template update before applying it. CloudFormation shows what will be added, changed, or removed, helping reduce risk during updates.
Source: Amazon
Challenges and limitations of IaC
While infrastructure as code offers significant automation and consistency benefits, it also introduces several challenges that organizations must address to fully realize its potential.
- Complexity and learning curve: IaC requires understanding both the infrastructure and the tools used to define it. Teams must learn domain-specific languages (DSLs), tool-specific behaviors, and cloud provider APIs. This learning curve can slow down adoption and increase the risk of misconfiguration if not carefully managed.
- Tooling fragmentation: There is no single standard for IaC. Different tools use different syntaxes and operate in different ways. Organizations may end up using multiple IaC tools across teams or projects, leading to inconsistency and difficulty in standardization and maintenance.
- State management: IaC tools must track the current state of infrastructure to apply changes accurately. Managing this state—especially in collaborative or multi-cloud environments—can be complex. Mistakes in state handling can lead to drift or unintended infrastructure changes.
- Security risks: As mentioned above, IaC templates can expose sensitive information such as credentials, API keys, or access permissions if not properly managed. Without strict access controls, versioning policies, and secret management practices, IaC files can become a security liability.
- Testing and validation: Unlike application code, infrastructure code is harder to test. There is no universal framework for IaC testing, and errors often surface only after deployment. Teams need to implement robust testing strategies using tools like policy-as-code frameworks (e.g., Open Policy Agent, Checkov) and dry-run capabilities to catch issues early.
- Cost overruns: IaC simplifies provisioning, but that ease can lead to over-provisioning or unused resources if not monitored. Without governance controls, teams may inadvertently increase cloud spend due to misconfigured or forgotten infrastructure components.
- Collaboration and governance: As infrastructure becomes code, collaboration challenges arise—especially around version control, code reviews, and approvals. Without clear policies and enforcement mechanisms, IaC changes may bypass critical checks, leading to operational issues.
Infrastructure as Code best practices
Deploying an IaC tool is the first step toward streamlining your deployment workflows. To ensure the success of your implementation, the following best practices can help:
Track versions of IaC definitions
Version control is essential for managing infrastructure as code. Store all configuration files in a source control system like Git to ensure traceability and reproducibility. Every infrastructure change should be committed with clear, descriptive messages that explain the intent and context of the update. Use branches and pull requests to isolate changes, conduct code reviews, and prevent unauthorized modifications.
By keeping a full history of infrastructure changes, teams can understand why a particular configuration was made, roll back to a previous known-good state if an issue arises, and audit modifications for compliance or security purposes. Integration with CI/CD pipelines allows automatic testing and validation of IaC changes before they are merged and deployed, reducing the risk of errors and misconfigurations.
Continuously test, integrate, and deploy
Testing infrastructure code should be part of every change lifecycle. Just like application code, IaC should be tested for syntax errors, policy violations, and configuration logic issues before deployment. Use static analysis tools (like terraform validate, cfn-lint, or ansible-lint) in your CI pipelines to catch issues early. Policy-as-code tools such as Open Policy Agent or Sentinel can enforce governance rules and security compliance.
To validate runtime behavior, deploy changes to ephemeral test environments or staging environments that mirror production. Use automated integration tests to verify that infrastructure components are deployed and working as expected. Integrate these steps into your CI/CD pipeline so that infrastructure changes are continuously tested, approved, and deployed in a reliable and repeatable manner.
Avoid IaC security risks
Security risks in IaC arise when misconfigurations, overly permissive policies, or hardcoded secrets are committed to configuration files. To mitigate these risks, embed security into every step of the IaC workflow. Scan templates with automated tools like Mend to detect vulnerabilities and misconfigurations. Enforce policy controls using tools like OPA or Regula to ensure infrastructure complies with organizational standards.
Secrets and credentials should never be stored in plain text within IaC files. Use secure secrets management systems like HashiCorp Vault, AWS Secrets Manager, or Azure Key Vault. Apply the principle of least privilege in your infrastructure definitions, granting only the permissions necessary for each resource. Control who can access and execute IaC code, and use audit logging to track changes and executions for accountability.
Modularize and reuse code
Large infrastructure projects benefit from modularity. Break your IaC into small, reusable modules that encapsulate specific functionality, such as creating a VPC, setting up IAM roles, or provisioning a database. Modules promote consistency, reduce code duplication, and make complex configurations easier to manage.
For example, in Terraform, you can create a vpc module used across multiple environments by simply passing in different variables. This approach also supports better testing, as modules can be validated independently before being integrated into larger systems. Organize modules into separate directories or repositories, and document their inputs, outputs, and dependencies to improve maintainability and usability across teams.
Implement proper state management
State files track the current state of your infrastructure, enabling tools like Terraform to determine what changes are needed. Mismanagement of state can result in failed deployments, drift, or resource conflicts. To avoid these issues, store state files in a shared, remote backend (such as AWS S3, Azure Blob Storage, or Terraform Cloud) with appropriate locking mechanisms to prevent concurrent updates.
Always enable encryption for stored state files, as they may contain sensitive data. Use access control policies to restrict who can read or modify state. Regularly back up your state files, and establish a process for recovering from corrupted or deleted state. For environments with multiple teams or modules, consider using separate state files to reduce risk and improve manageability. Proper state management is critical for maintaining a reliable, predictable IaC workflow.
Infrastructure as Code and DevOps success
The promise of IaC is in its ability to standardize all cloud configuration processes to maximize efficiency and minimize costs. Automation of infrastructure is now a major requirement for all organizations. As modern applications move more and more to the cloud, IaC will take on even greater importance.
When selecting an IaC tool, always keep security top of mind. Look for solutions that help organizations secure IaC templates and check for security issues, compliance violations, and other misconfigurations. The best solutions are those that allow developers to detect, track, and fix the misconfigurations as part of their normal workflow without leaving their code repositories to view results or set up a separate workflow to scan. A solution that puts security first gives security admins the confidence they need in IaC built and operated by DevOps.